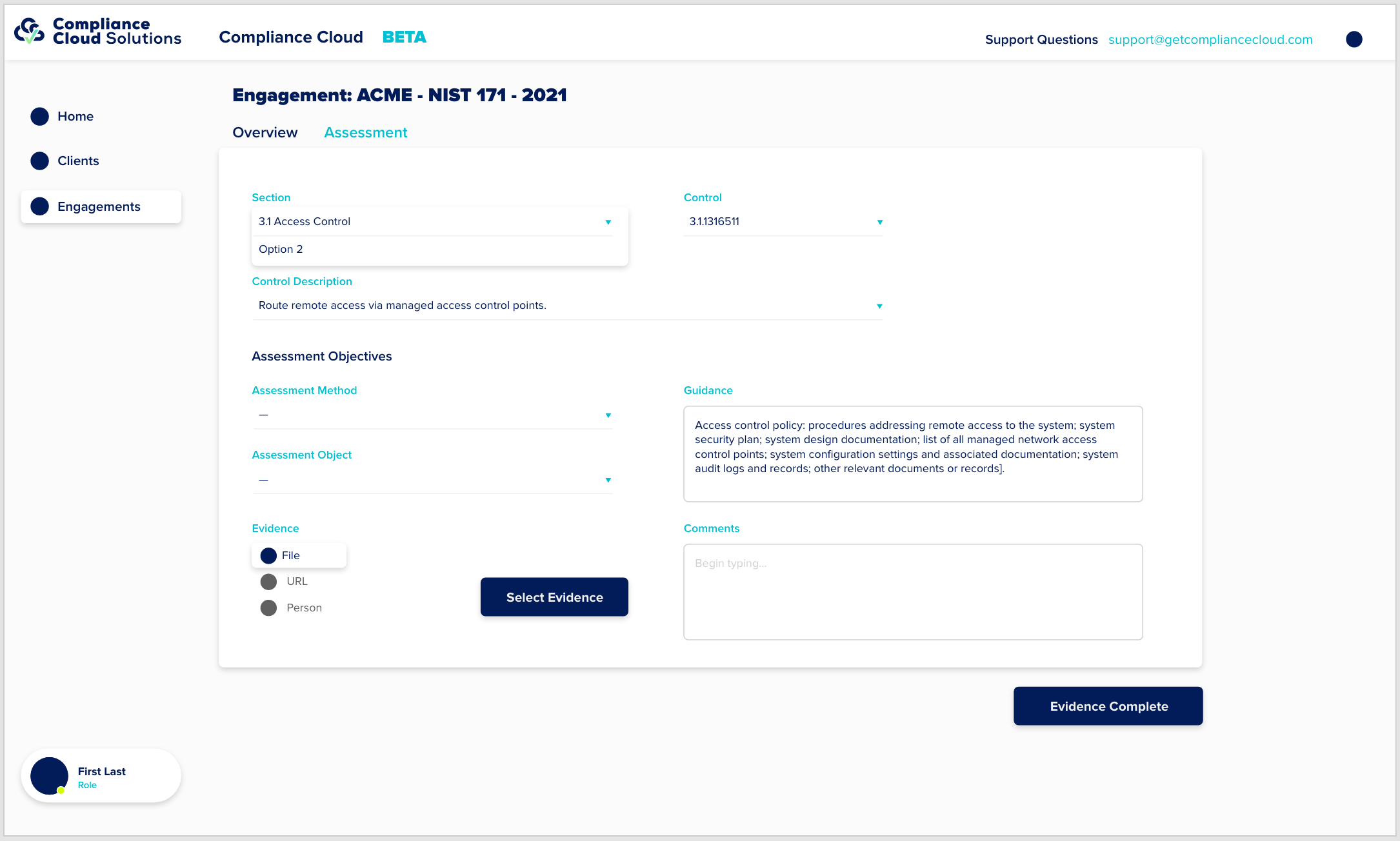
The Environmental Profile The first step in completing your assessment is documenting the technical environment. Compliance Cloud does this independently of any control framework. Complete a profile and upload the relevant information about your environment, and we map it to each control.